In this Trezor Safe 5 review, we will cover the latest hardware wallet by Trezor and its pros, cons, and features, to help you determine if this wallet is the one for you.
Crypto security is vitally important and a topic that we here at 99Bitcoins are very passionate about, and it is easy to understand why. I don’t know many fellow crypto enthusiasts who have spent any significant time in crypto without the battle scars of lost funds to prove it. Whether it was the insolvency of Celsius, BlockFi, or FTX that burned us, software wallet hacks such as the Atomic Wallet fiasco, the collapse of Terra Luna, or even the $230 million WazirX hack that is being investigated as I write this, crypto can be a dangerous place if we don’t take precautions.
Crypto hardware wallet sales have skyrocketed as trust in centralized entities has crumbled and security incidences have risen, with Trezor being among the industry leaders with their pioneering Trezor One, Model T, and their newer flagship products the Trezor Safe 3 and Trezor Safe 5.
At 99Bitcoins, we march to the tune of self-custody and preach the safety of hardware wallets, which is why we are happy to be bringing you this Trezor review today.
Key Features of the Trezor Safe 5:
- Price: $165
- CE and RoHS security-certified EAL6+ Security Chip.
- Open Source
- Pin & Passphrase Protection
- Color Touchscreen
- Gorilla Glass for scratch resistance and durability
- Anodized Aluminum Body
- Send, Receive, Stake and Trade Crypto
- Over 9,000 Assets Supported
- MicroSD Card Slot
- Available for Mac, Windows, Linux, Android, and iOS (iOS is View Only)
Trezor Safe 5 Review Summary
The Trezor Safe 5 is the latest flagship hardware wallet from Trezor and is based on the design of the highly popular Trezor Model T, albeit, with some upgrades.
The Safe 5 boasts a beautiful design, compact size, and support for over 9,000 assets. It features a highly secure EAL6+ NDA-free secure element, marking a significant improvement over the older Model One and T versions. This advancement, along with the Trezor Safe 3, sets it apart from competitors like Ledger and ELLIPAL. The Safe 5 features a color touchscreen and is the most durable Trezor hardware wallet to date thanks to the anodized aluminum body and Gorilla Glass touchscreen.
That sums up the Trezor Safe 5 from a high level, but read on if you want a more detailed review of our experience with the Trezor Safe 5.
What is The Trezor Safe 5? Initial Impressions
The Trezor Safe 5 is the latest self-custodial hardware wallet from Trezor, the iconic crypto wallet company owned by Satoshi Labs.
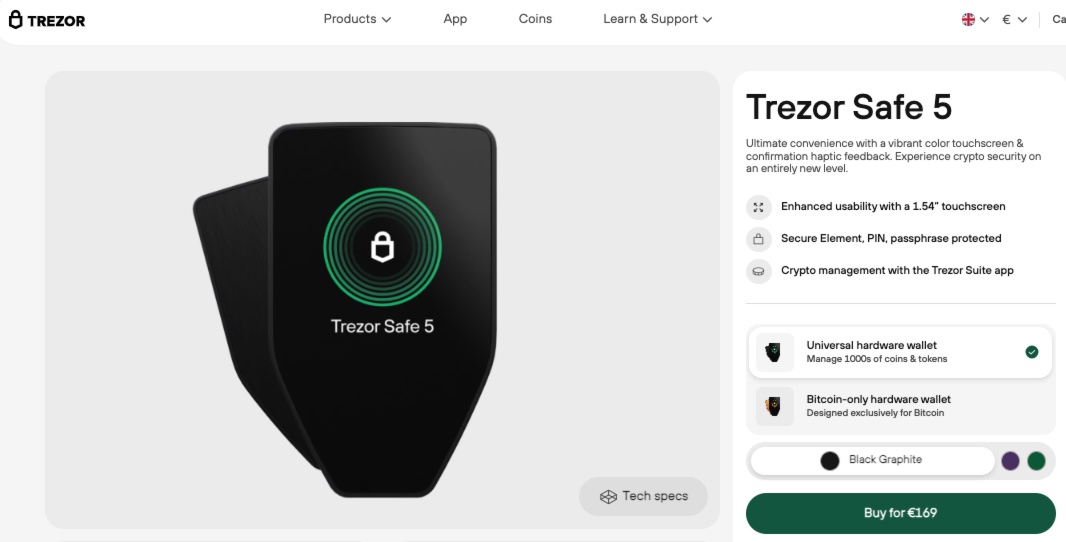
The Safe 5 features a vibrant color touchscreen and tactile feedback, making it super intuitive to use. Built on a decade of open-source security development, it uses the NDA-free EAL 6+ Secure Element, along with PIN and passphrase protection to guard against online and offline threats. The upgraded 20-word wallet backup standard offers more sophisticated recovery options for advanced users.
That was a lot of jargon in that last paragraph, don’t worry, we will break down what all of that means in later sections.
The Trezor Safe 5 integrates seamlessly with the Trezor ecosystem through the Trezor Suite desktop and mobile apps, which make it easy to buy, sell, and exchange cryptocurrencies. Plus, it supports various third-party services for additional wallet support and access to DeFi and Dapps, making it perfect for both beginners and seasoned users.
The folks over at Trezor were kind enough to send us their latest product for unboxing, testing, and reviewing. We have reviewed every wallet Trezor has ever released, and have always been fans of their products, which is why Trezor wallets have been featured in both our Best Hardware Wallets and Best Bitcoin Wallets Guides, but regardless, we will keep this review unbiased and impartial as possible.

Upon opening the box and picking up the Safe 5, as with the Safe 3, the first thing that stands out is its premium quality, both Safe products feel durable and solid. In my Trezor One and Model T reviews, although I reviewed them favorably, my main criticism was always how flimsy they felt. I always felt like I had to handle the Model T with the fragility of a cracked egg.

It seems they took that criticism to heart as they have significantly beefed up not only the security but durability of their new product line. The Safe 5 is a good size, conveniently fits in the palm of your hand, and as mentioned, feels solid, let’s pause on that last point for a moment. Taking durability to the next level, the Trezor Safe 5 uses Gorilla Glass for the touch screen on this device, which is the highest-rated touch screen glass on the market in terms of strength and being scratch-proof.
The back of the device is made with anodized aluminum, giving the Safe 5 a much more premium feel and build than previous Trezor versions. When comparing the Safe 5 to the previous Model T touchscreen, the Safe 5 also doesn’t have a plastic border around the screen, giving it a much sleeker feel and design.

The Trezor Safe 5 can be ordered in four different colors:
- Bitcoin Orange
- Black Graphite
- Violet Ore
- Green Beryl
Users can also choose to order the Bitcoin-only version or the multi-coin version. The Bitcoin-only model uses Bitcoin-only firmware for those only interested in BTC while the standard version supports Bitcoin as well as multiple other coins.
After using other touchscreen wallets like the ELLIPAL Titan, NGRAVE ZERO, and the Model T, I must say this is the most responsive touchscreen wallet I’ve used and the haptic vibration feedback is a nice little addition to confirm key hits and confirmations.
Trezor Safe 5 Specs:
- Product size: 65.9x40x8 mm/ 2.6×1.6×0.3 in
- Weight: 23 g/ 0.8 oz
- Operating Temperature: -20°C to +60°C / -4°F to +140°F
- CPU: 160MHz embedded ARM processor (Cortex M33)
- Material: Durable PC-ABS plastic, tamper-evident casing, anodized aluminum backplates, and intricate laser engraving
- Touchscreen: 1.54” Color display 240 x 240 pixels
Trezor Safe 5 Security
Before using any Trezor cold storage wallets. it is important to ask yourself “Is Trezor Safe?”
A great first step in determining whether or not Trezor is safe, secure, and dependable, is to take a moment to cover the team behind Trezor hardware wallets.
Trezor devices are crafted by Satoshi Labs, a company based in Prague in the Czech Republic. Satoshi Labs, founded in 2013 by Pavol Rusnak, Marek Palatinus, and Alena Vránová, has been on the cutting edge of secure solutions for safely storing private keys. The industry widely considers Satoshi Labs to be one of the most trustworthy and dependable companies. Since the early days, Satoshi Labs has been a true cornerstone in cryptographic development and security, innovating and pushing forward the blockchain industry.
In 2014, Satoshi Labs released the Trezor One, the first cryptocurrency hardware wallet to hit the market, marking a significant milestone in crypto history. Since then, millions of Trezors have been sold worldwide to customers in over 150 countries to become the best-selling crypto hardware wallet company in the world. The track record is also impeccable, with no known cases of remote hacks or security breaches ever recorded on their devices. It is worth noting two security events that have happened though. We mentioned that there have been no successful remote hacks, but a few years ago, sophisticated hackers uncovered a method to break into older Trezor models using what is known as a voltage-glitching technique.
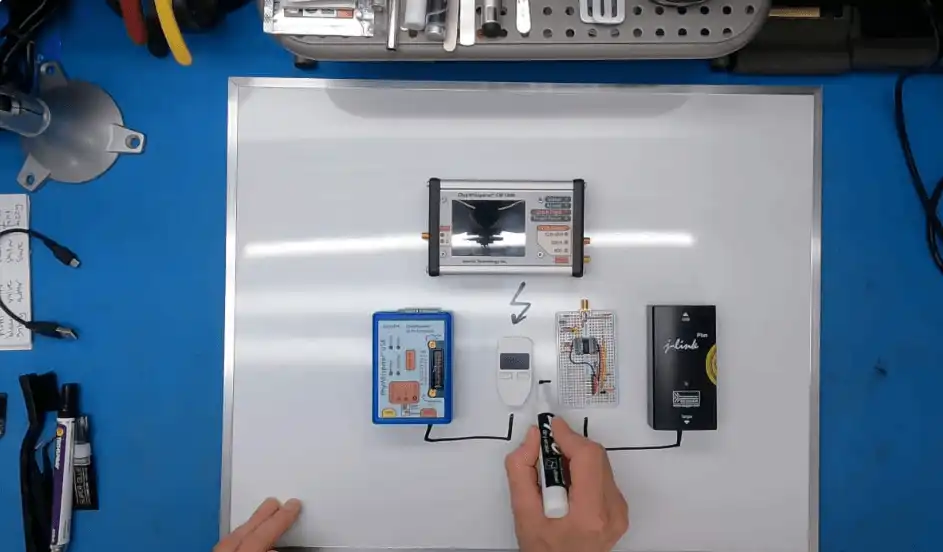
Understandably, this caused concern from some Trezor users but many felt this concern was overblown as it would require hackers to somehow get their hands on a user’s Trezor and have the technology needed to break into it. It wasn’t just Trezor that got caught out with this technique, similar techniques were used to break into old Ledger and ELLIPAL wallets as well. Trezor’s response to this was the release of the Safe 3 and Safe 5, which feature a more secure chip, rendering this technique ineffective.
The second event was in early 2024, Trezor’s X Account was hacked and tricked some users into taking part in a fake token sale. Unfortunately, X account hacks have become commonplace with the Twitter accounts of presidents, celebrities, and even the likes of Bill Gates and Jeff Bezos being taken over so it seems nobody is safe. Just goes to show that you need to be careful with what you read and choose to click on when diving into the world of X posts.
Those two events aside, the fact that there have been zero remote Trezor hacks to date and their stance on transparency and open-source principles stand as a testament to what makes Trezor a beacon of trust and why they carry a sterling reputation among the crypto community.
Side Note– The concept of how hardware wallets work and what makes them the best choice for crypto security is outside the scope of this review, feel check out our article Hardware Wallets Explained if you want to go into the details of these devices.
Now, let’s get into the security features.
MicroSD Card
The side of the wallet features a slot for a microSD card (not included) which is an optional feature to enhance the security of your wallet against physical attacks. When enabled, a randomly generated secret is stored on the microSD card and essentially binds with the PIN you set for your device.
This means that the device cannot be unlocked without the accompanying microSD card. This could be a good way to implement geo-separated security, keeping the wallet and card in separate locations.
If you lose the MicroSD card, you can still access the wallet by disabling the feature in your wallet or simply doing a factory reset of the device and using your recovery phrase.
NDA-Free EAL6+ Secure Element
This state-of-the-art secure element provides not only a highly secure, but transparent method for keeping your private keys secured. The choice to go with the absence of a non-disclosure agreement (NDA) shows Trezor’s commitment to openness and trust that goes alongside their open-source ethos.

This addition is in no doubt a response, some would say a “check-mate” to Ledger’s recent blunders that awakened (and outraged) the crypto industry to the dangers and security concerns that lurk behind closed source software. Open source software and transparency are a core ethos of crypto and adhere to our credo “don’t trust, verify,” so a big pat on the back here for the Trezor team, nice one.
Trezor is the only wallet that I am aware of that offers an NDA-Free secure element, making this wallet 100% open source, a claim that competitors cannot match.
Bootloader Verification
When you plug in and fire up your Trezor Safe 5, you will see what is known as a Bootloader Verification.
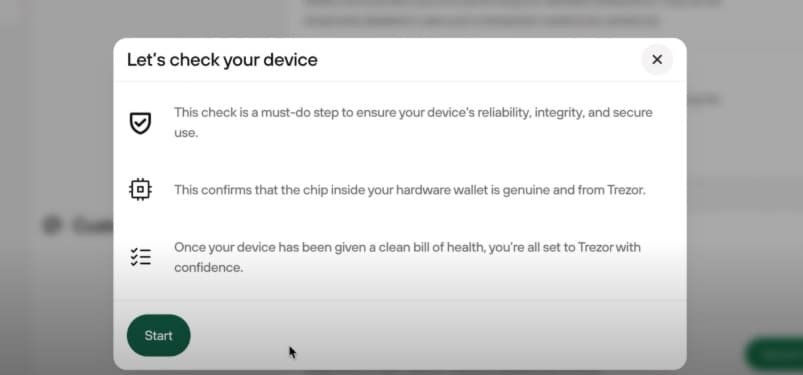
Anytime you plug your device into a computer this check runs to ensure the firmware on your device is authentic and the wallet is not running any compromised software. It’s a nice additional check to provide you with some peace of mind.
Hidden Wallet
During setup, you will be able to create a “Hidden Wallet” also known as a passphrase.
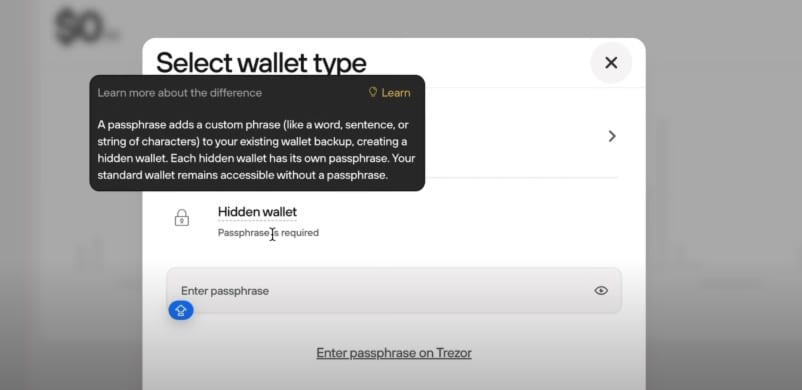
This allows you to add an additional secret word, known only by you, to secure your wallet. This means that even if someone found your 12, 20, or 24-word recovery phrase, they would not be able to access the funds without knowing the passphrase for the hidden wallet.
Pro Tip!: Be VERY careful when using the passprhase feature as nobody can help you recover your wallet if you forget or lose the passphrase. Mishandling this, or your recovery phrase can result in a complete and irrecoverable loss of funds.
The way I would recommend using this feature is to write down your recovery phrase, as you normally would, and add a passphrase, a word that you will never forget and that a hacker is unlikely to guess.
Pin and Passphrase Protection
Users will be prompted to secure the device with a pin, which should be something harder to guess than “1234”. Come on, don’t be that person. To prevent unauthorized access to your device, you are going to want to set a PIN that you will remember that nobody else will know.
The passphrase allows you to create the hidden wallet, which we described above. One feature I especially like about Trezor wallets is that you can choose to enter your PIN on the device itself instead of your computer when trying to access the wallet. I always recommend this method to avoid the risk of potential keylogging malware that may exist on your computer, which can read the keystrokes on your computer, potentially exposing your PIN to prying eyes.
And this is a good opportunity to address a concern that is asked by many crypto users considering using a hardware wallet:
“Do I need to worry about viruses on my computer when using a hardware wallet?”
No! That is one of the most beautiful things about hardware wallets and what makes them substantially more secure than software, desktop, or mobile wallets. The secure and sensitive information required to access your crypto is encrypted in the secure element chip in the wallet itself, and the connected computer never receives that information. All transaction signing also happens on the Trezor cold storage wallet itself, not the computer. This means that your computer could be infected with every virus known to humanity from all those questionable websites you probably shouldn’t be visiting and still use a Trezor wallet safely.
This is in stark contrast to how software wallets work as the private keys are encrypted on the device with internet access. The #1 risk to crypto holders is remote attacks from hackers who can infect a computer or phone with a virus that could expose private and sensitive information. And it isn’t just our opinion that hardware wallets are the best choice in crypto security, here is a quote from the security experts over at Kaspersky regarding hardware wallet security:
“Of all the software and hardware choices out there, a hardware wallet is one of the simplest and most effective ways to store your currency” –Source
As Trezor hardware wallets have zero internet connectivity, there is no attack surface for hackers to exploit.
Trezor Safe 5 Review: Features and Functions
Now we will get into some of the features and functions of the Trezor Safe 5.
Buy, Sell, and Swap Crypto with Trezor Suite
As with all Trezor cold storage wallets, the Safe 5 operates with Trezor Suite, the accompanying desktop or mobile software that allows users to buy, sell, swap, send and receive crypto, and manage their crypto portfolios.
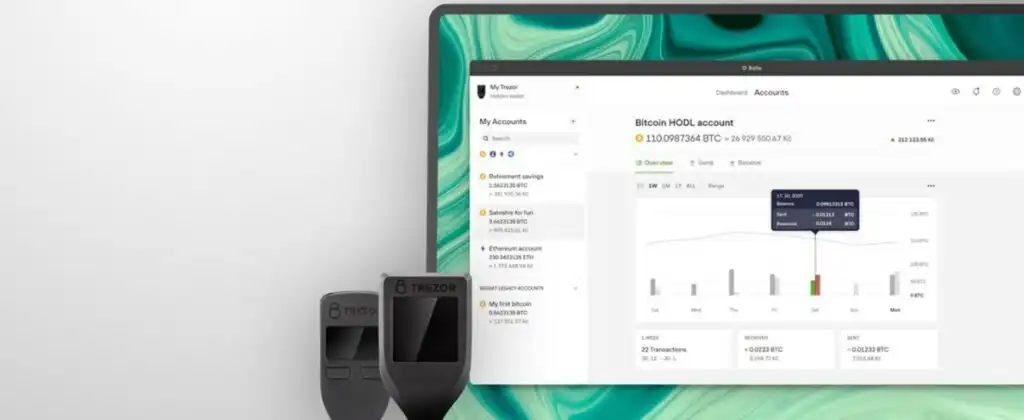
Trezor Suite is an easy-to-use platform that can seem daunting at first, but after clicking around for a few minutes, users often find that Trezor Suite is a great blend of simplicity and functionality. There aren’t a lot of bells and whistles, just the functionality that crypto users need to manage and track their crypto portfolios. Trezor offers some great videos on how to use Trezor Suite which you can find on the Trezor YouTube Channel.
Trezor Suite Features:
- Tor Network– Added privacy feature that makes it difficult to trace your internet activity
- Coin Control– Gives users more control and enhanced privacy when sending funds
- Taproot– Enhances Bitcoin safety, privacy, and network efficiency
- Discreet Mode– Hide sensitive information on screen
- Language Support– English, Spanish, Russian, Japanese, Czech
- Export and Labelling Transactions
Backup and Recovery
Upon setting up the wallet, the Trezor will create a unique 20-word seed phrase that allows for enhanced recovery options, alternatively, users can also import a standard 12 or 24-word recovery phrase. All Trezor devices come with two cards to write your recovery phrase on, the Trezor Safe 5 comes with cards that support the 20-word phrase.

If you ever need to recover your crypto in the event of a lost or damaged Trezor wallet, simply enter your recovery phrase into a new wallet and you will regain access to your crypto.
New SLIP39 Multi-Share Backup Method
This version of the Shamir Backup Method allows users to fragment their backups and store them in separate places, requiring a certain threshold of fragments to recover the wallet.
What this does is ensure that there is no single point of failure with a single recovery phrase. Most wallets require you to back them up by writing a recovery phrase on a piece of paper. If someone finds that paper or you lose it, you can permanently lose access to your funds.
What the SLIP39 multi-share backup allows users to do is break up the recovery phrase and store it in different locations, needing a threshold of 2 or more to come together to recover the funds.
Here is an example of how this increases security. Say you want to set up a 3 of 5 Shamir Backup system. You hold one set, give one to a friend, one to your mom, one to your brother, and keep one in a bank vault. Nobody can access your funds with just one of these pieces. You would need to have access to any of the 3 of 5 to create a recoverable backup.

The key difference between the SLIP39 backup method and the Shamir Secret Sharing backup method is that with SLIP39, users can initially set up their wallet using a 20-word seed phrase single backup and later upgrade to a multi-share backup. You need to complete the traditional Shamir backup during the initial setup.
Important Note– If you choose to use the SLIP39 backup method, you will be reliant on future Trezor devices to recover your wallet should your Trezor become lost or damaged as other wallets on the market do not support this backup method at this time.
Trezor Supported Cryptocurrencies
Trezor’s latest wallet supports over 9,000 coins and tokens, including Bitcoin, Ethereum, Cardano, Ripple, BNB, and all ERC-20 tokens. Recently, the Safe 5 added support for Solana and all SPL tokens. Note that some notable networks like Cosmos and Avalanche aren’t supported yet. The Safe 5 can also integrate seamlessly with third-party software wallets like MetaMask, MyCrypto, Ronin, MyEtherWallet, and many more, enhancing asset support and the ability to interact with DApps and DeFi.
The Trezor Keep Metal
An optional purchase Trezor users can make if they want to take their security to the next level is the Keep Metal.
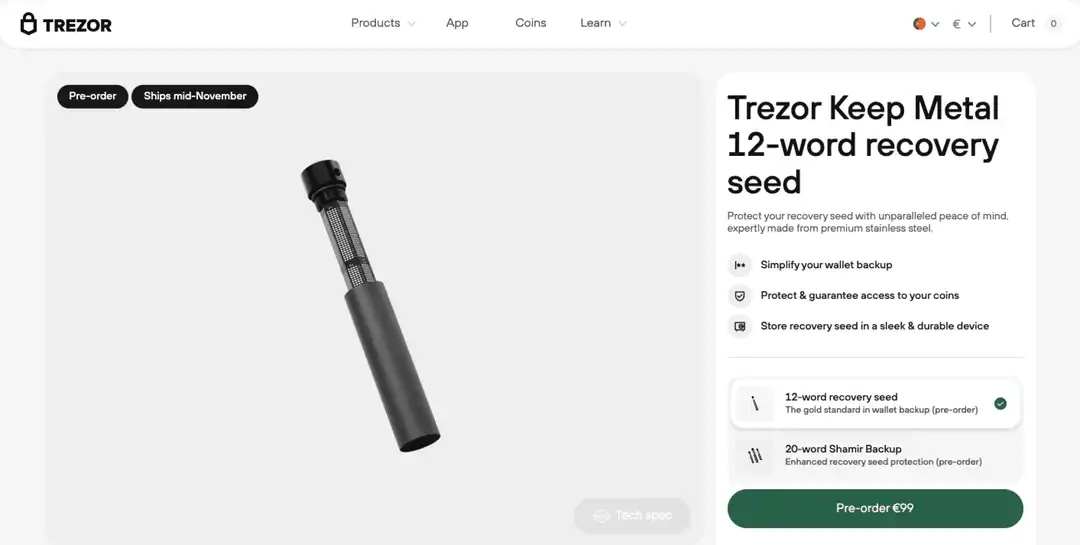
Users can purchase one to keep their seedphrases secure. The way it works is the user punches the first four letters of each of their seed words into the metal using the metal punch that comes with the device and viola. Instead of keeping something as precious and important as a recovery phrase written down on a fragile piece of paper, why not punch it into metal, which is fireproof, waterproof, and pretty much apocalypse-proof? An interesting additional touch is it also comes with security stickers to seal the device so you will know if anyone opened it.
Trezor Safe 3 vs Trezor Safe 5
The Safe 5 rings in at $90 more than the Safe 3 and really, the only major benefit here is the convenience of the touch screen. while the Safe 3 uses two buttons to navigate, which can make tasks such as adding in a recovery phrase or typing in anything slow and tedious. The Safe 5 is much quicker and more responsive, but it will be up to the user to decide if the benefit of a touch screen is worth the extra 90 bucks.
| Trezor Safe 3 | Trezor Safe 5 | |
| Price | $79 | $165 |
| Touchscreen | No | Yes |
| Asset Support | 9,000+ | 9,000+ |
| MicroSD Card Slot | No | Yes |
| Display | 0.96″ Monochromatic display | 1.54″ Color Display |
| Gorilla Glass | No | Yes |
| Security Chip | Certified Chip EAL6+ | Certified Chip EAL6+ |
| Open Source | Yes | Yes |
| Pin & Passphrase | Yes | Yes |
| Backup & Recovery | 12, 24, and 20-word wallet backups. Optional Advanced Multi-share Backup | 12, 24, and 20-word wallet backups. Optional Advanced Multi-share Backup |
| Privacy Features | Coin Control & Tor | Coin Control & Tor |
How to Set Up the Trezor Safe 5
Anyone who has set up a previous Trezor device will find this pretty straightforward as the setup and installation of all Trezor wallets are initially the same. If you prefer to watch a video about the setup, check out Trezor’s video on How to Set Up a Trezor Safe 5.
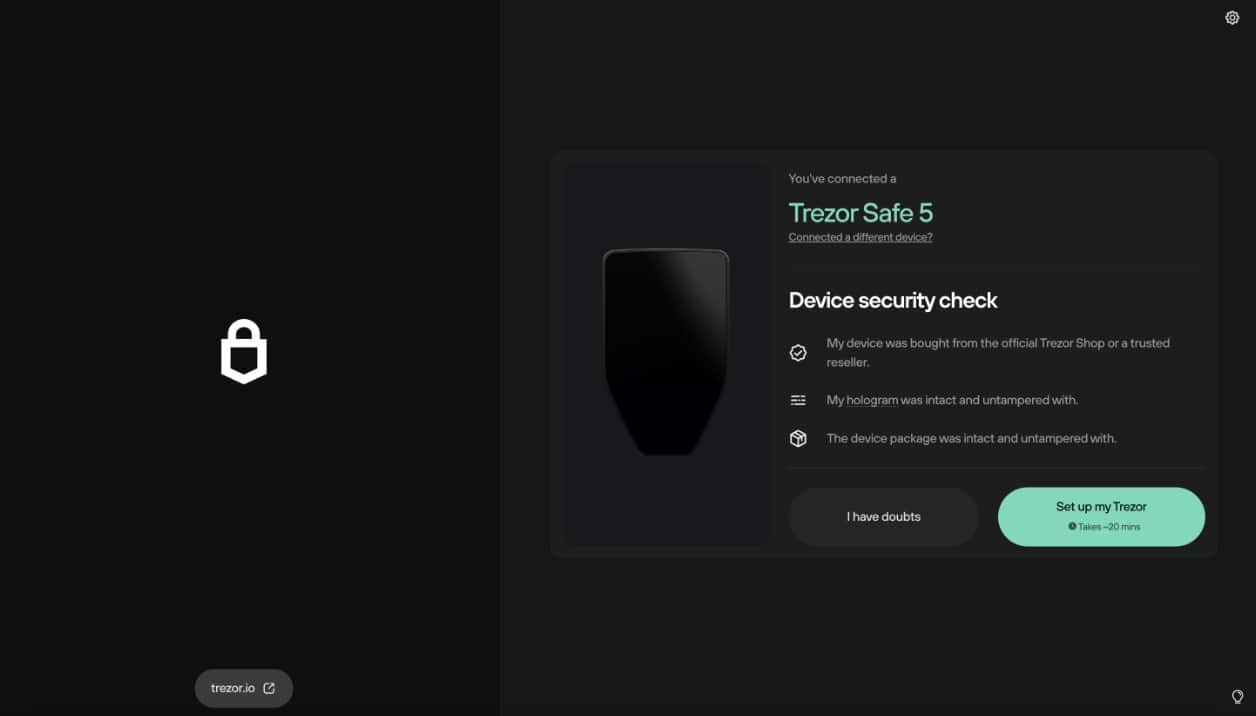
Once you take off the security holographic tape that verifies nobody tampered with your device during transit, you are going to want to plug your Trezor device into your laptop.

Your Trezor will tell you to go to Trezor.io/start, which is where you will download the desktop app needed to use your hardware wallet. The Trezor Suite software is available for:
- Mac
- Windows
- Linux
- Android and iOS (iOS is view only)
After you install the Trezor Suite software (or use Trezor Suite for Web), the software will prompt you to “Set up my Trezor.”
This step will guide you to install the firmware since Trezor ships without it. After completing the firmware installation, click “continue.”
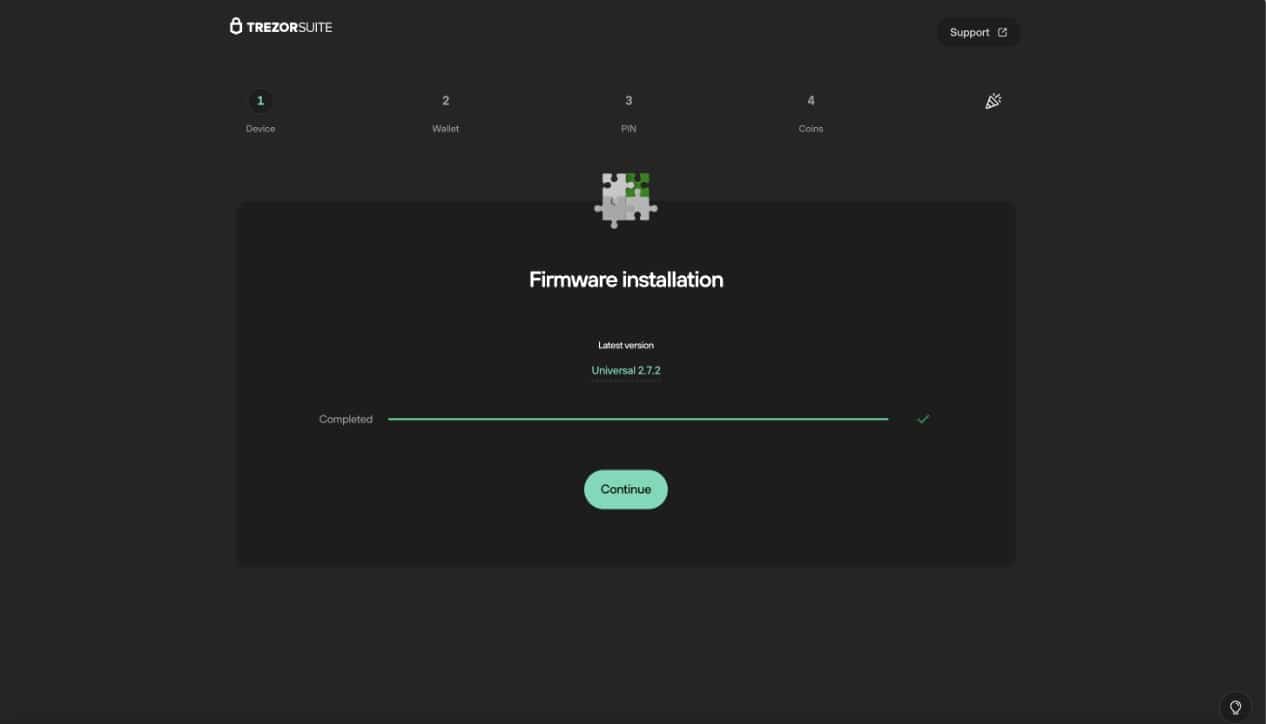
Next, the software will verify that your device is an authentic Trezor wallet and has not been tampered with. After it performs this check, you will hit continue.
Now you will need to either create a new wallet or recover an existing wallet if you should choose. For most people, you will likely be creating a new wallet.
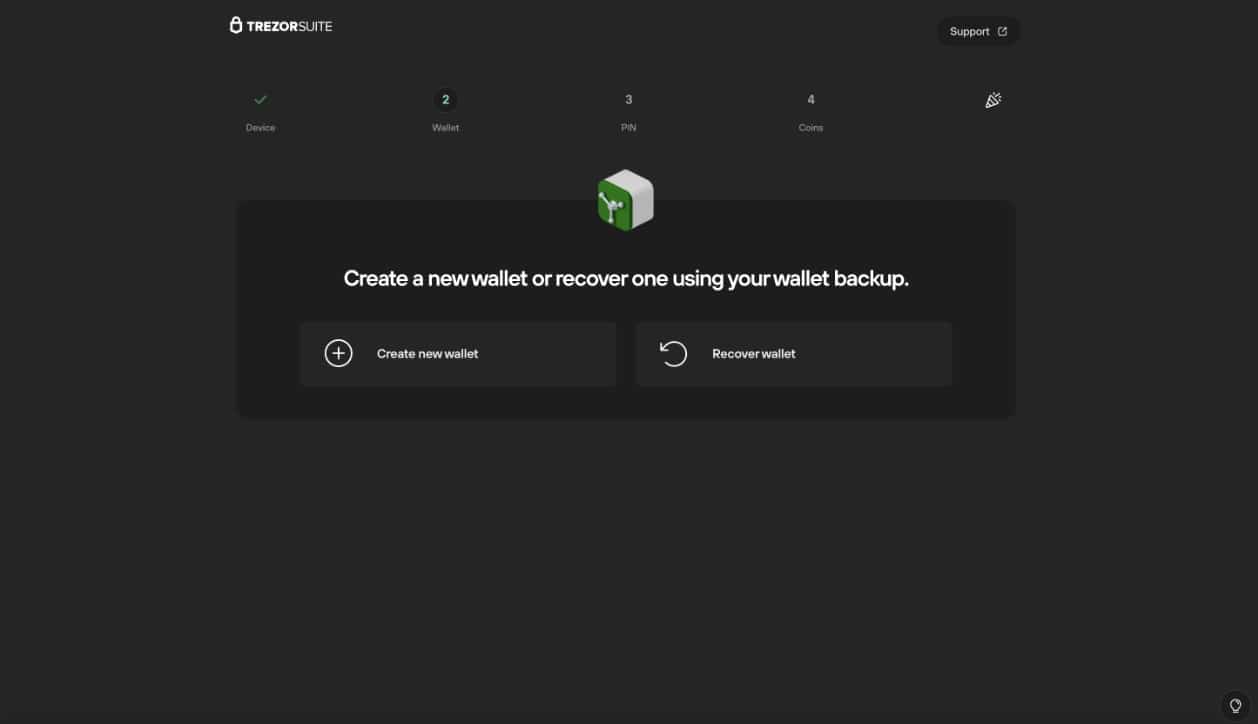
Here is the step where you will choose between single-share backup or multi-share backup. As single-share backup is the most common and widely used, this guide will be focusing on that. If you want to learn more about the multi-share backup, you can find Trezor’s article on Multi-Share SLIP39 Backup.
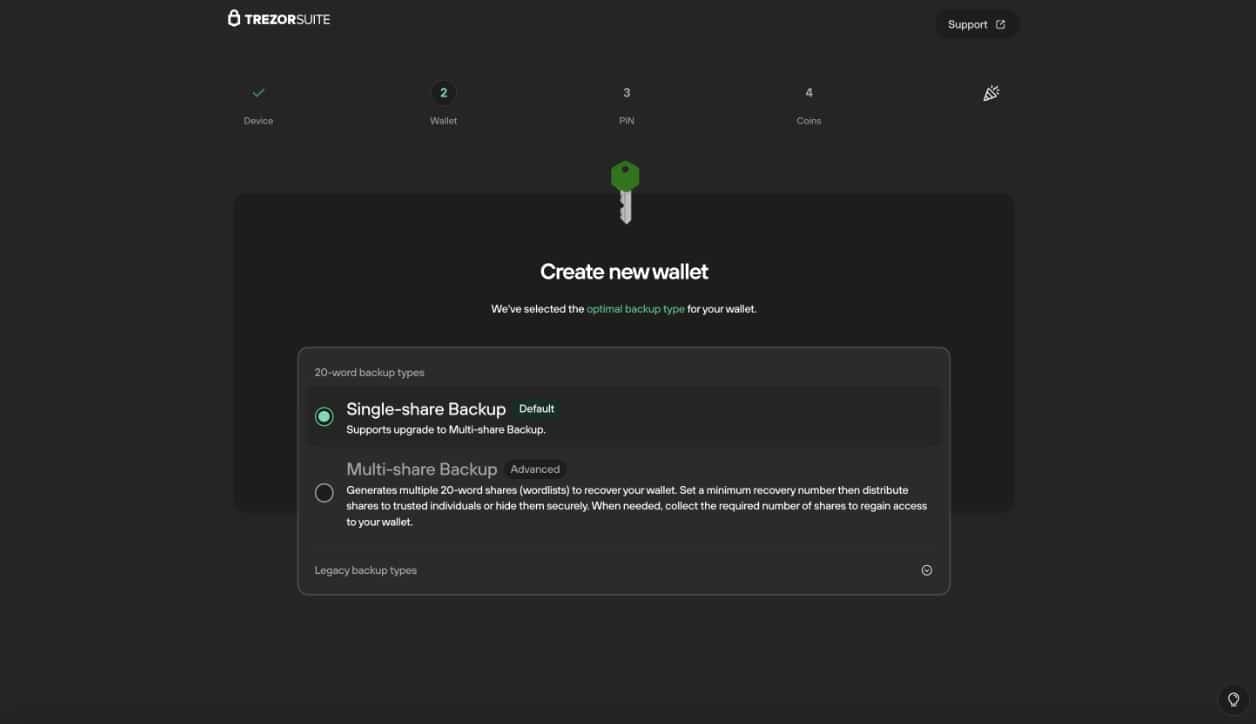
Now you will see a screen that says “Wallet Successfully Created” and you will continue to backup. Creating a backup is the most important step when it comes to crypto storage, be sure you are in an environment with no distractions, no cameras, and you double, triple, and even quadruple-check your recovery phrase as you write it down on paper. If you make a mistake here, you may never be able to recover your funds.
Pro Tip– Write your backup down on paper or use a metal backup method such as the Trezor Keep Metal, but NEVER keep a digital copy of your recovery phrase. Do not photograph or store the recovery phrase anywhere online! There have been multiple stories of Google Drive, Apple iCloud, and One Drive account breaches that have resulted in stolen crypto as users decided to store their recovery phrases online. Even the password manager LastPass was hacked, resulting in millions worth of stolen crypto as users thought password managers were a good place to keep their recovery phrase backups. If you store a recovery phrase online, it completely negates the purpose of using a hardware wallet at all.
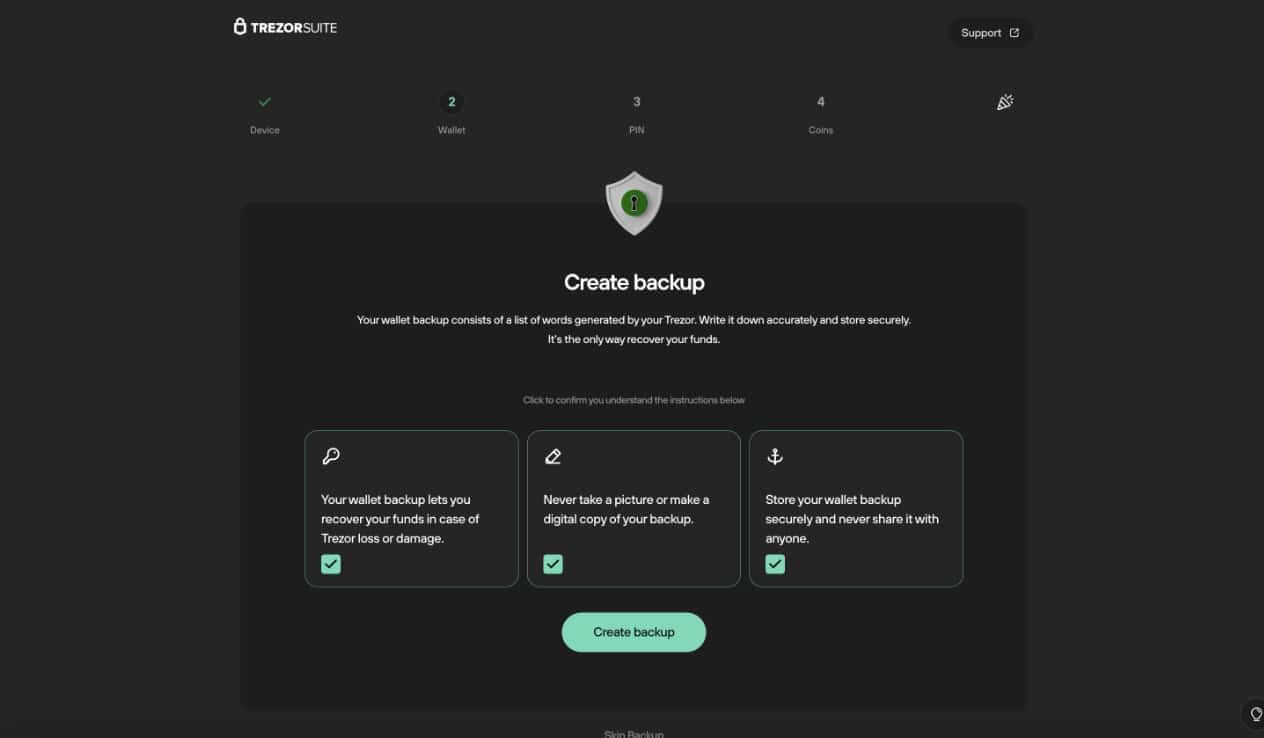
After you create the backup and write down all your recovery phrase words, the device will ask you to confirm the backup by entering the words back in the correct order.
After you complete the most important step, the device will ask you to create a PIN. Be sure to choose a strong PIN that you can remember.
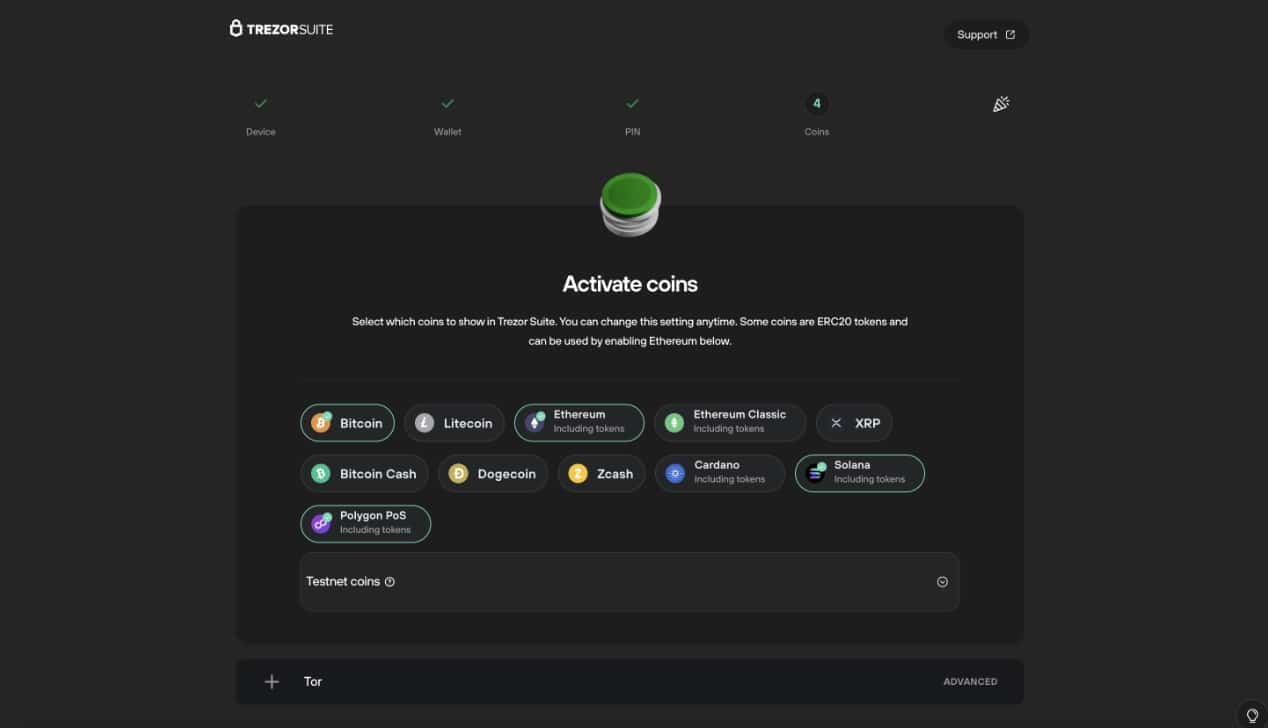
You are almost there. Now you can select the coins you wish to activate. Don’t worry about future cryptocurrencies you may want to hold, you can always activate more later.
Bonus Expert Tip- One of the most surefire ways to make sure you have your recovery phrase written down correctly is once the wallet is set up and good to go, before funding it with crypto, write down your Bitcoin receiving address, then factory reset your Trezor device. Once it’s reset, recover your previous wallet with your recovery phrase and check to make sure the Bitcoin address matches. Trust me on this one, even after setting up dozens of crypto wallets myself, I made this mistake once of writing the words down wrong as I mixed up the words “claim” and “calm”. I also know quite a few other crypto veterans who have made similar errors even after years in the industry, some leading to devastating losses, so don’t think it can’t happen to you.
You will now see a screen confirming that the setup is complete. Before you can access Trezor Suite, the device will ask you to select a wallet type, which refers to the hidden wallet feature we discussed earlier.
Make your choice and that is it! The Trezor Suite interface will now appear, where you can find your wallet addresses and buy, sell, send, receive, and swap cryptocurrencies.
Trezor Safe 5 Review: Closing Thoughts
Trezor devices continue to get better and better over the years, and the Safe 5 is no exception. After witnessing the evolution of these wallets from the Trezor One to the Safe 5, I am impressed with how the Trezor team has focused on creating not only more durable but also more secure products.. The introduction of the enhanced security chip without the NDA is quite the head-turner and as someone who appreciates open-source code and transparency, the Safe lineup of wallets has found a place in my collection for storing my most precious digital assets.
FAQs
Is Trezor Safe and Can Trezor be Trusted?
Yes, Trezor is one of the longest-standing and most reputable hardware wallet manufacturers in the world. The majority of the crypto community respects and trusts Satoshi Labs, the company behind the Trezor wallets. The Trezor team dedicates itself to cryptographic secure solutions and maintains a reputation for open-source principles and transparency.
Is Trezor Wallet Worth It?
For users who want to take the security of their crypto seriously, an investment in a Trezor wallet can be one of the best choices crypto holders can take. Many crypto veterans will take a similar approach to this when it comes to crypto storage strategies:
Keeping crypto on an exchange– This approach should only be considered for users who are actively trading frequently. This is the highest risk as keeping funds on an exchange exposes crypto holders to third-party custody risk and exchanges are popular targets for hackers.
Software wallets/hot wallets such as MetaMask or Mobile Wallet– Crypto users who need frequent access to DApps and DeFi often utilize software wallets. This poses a higher risk than using hardware wallets because devices with internet connectivity connect to software wallets, making them more vulnerable to phishing attacks, hacks, and scams. You can think of software wallets similarly to your physical wallet—you don’t carry your life savings in your leather wallet, just your “walking around” money. Treat software wallets the same way, and avoid storing significant amounts of wealth in them.
Hardware Wallets– This is the most secure solution as these devices do not have online connectivity and have no attack surfaces to exploit remotely. Use these devices for long-term crypto storage and larger amounts. People often compare hardware wallets to bank vaults or safes for storing larger amounts of wealth.
Trezor vs Ledger: Is Trezor Better than Ledger?
It is of my opinion that Trezor is better than Ledger. While both are well known for making high-quality crypto storage wallets, Ledger has lost significant trust and damaged its reputation in the crypto community. The data breach, the PR disaster with Ledger Recover, the antagonistic response to user outrage, the avoidance of open-source principles, and the Ledger Connect hack have all turned many users away from Ledger.
What is the Safest Hardware Wallet?
This question is up for debate, but many feel that Trezor is the safest hardware wallet thanks to its long-standing track record, reputation, open-source approach, and flawless track record. Others feel that air-gapped wallets are the way to go, favoring wallets such as ELLIPAL and NGRAVE Zero. Another camp is those who feel that Multi-Party Computation (MPC) wallets are the best approach so they favor wallets such as Zengo. Many crypto veterans will split their risk across multiple wallets to avoid single point of failure risk. Personally, I highly recommend using a mix of wallets such as a Trezor, and keeping some funds in a Zengo wallet as it’s free! (no reason not to). You can learn more about Zengo in our Zengo review.
Can Trezor Be Hacked?
To date, there have been no known successful remote hacks. Before the Trezor Safe 3 and Safe 5, sophisticated hackers with advanced equipment could hack into physical Trezor devices in their possession. However, the improved secure element chip has removed this attack vector.
See Also: Which Crypto is Set to Explode in 2024? Our Top Picks!
References:
“WazirX $230M Hack Spot Ether ETFs.” Techopedia: https://www.techopedia.com/news/wazirx-230m-hack-spot-ether-etfs
“Crypto Atomic Wallet Faces Class Action Over $100M Crypto Hack Losses.” Cointelegraph, https://cointelegraph.com/news/crypto-atomic-wallet-faces-class-action-over-100m-crypto-hack-losses.
“Hackers Take Over Crypto Hardware Wallet Trezor’s X Account – What’s Going On?” CryptoNews, https://cryptonews.com/news/hackers-take-over-crypto-hardware-wallet-trezors-x-account-whats-going-on.htm
“Twitter Account Hijacking.” Wikipedia, 29 July 2024, https://en.wikipedia.org/wiki/2020_Twitter_account_hijacking
“Crypto Wallet Provider Ledger Postpones Release of Key Recovery Service After Public Criticism.” CoinDesk, 23 May 2023, https://www.coindesk.com/business/2023/05/23/crypto-wallet-provider-ledger-postpones-release-of-key-recovery-service-after-public-criticism/
“£200,000 Stolen in Crypto by Hacking into Tech CEO’s iCloud Account.” Metro, 8 Aug. 2022, https://metro.co.uk/2022/08/08/200000-stolen-in-crypto-by-hacking-into-tech-ceos-icloud-account-17147708/
“LastPass Hack Victims Lose $44M in a Single Day.” CoinDesk, 30 Oct. 2023, https://www.coindesk.com/business/2023/10/30/lastpass-hack-victims-lose-44m-in-a-single-day/


